Use Case
Healthcare
For the 11th consecutive year, the healthcare market has the highest average data breach costs
Data breach costs in the healthcare sector increased from an average total cost of $7.13 million in 2020 to $9.23 million in 2021, a rise of 29.5%
An Appealing Target
The healthcare industry was the target of hundreds of cyber-attacks in 2021. Data breach reports the exposure of tens of millions of health records to unauthorized parties.
Massive data breaches cause ransomware attacks. Hospitals are perfect targets as they have large amounts of data that cyber-criminals can encrypt and weak defenses to prevent attacks. Hackers tend to attack the healthcare market as the industry deals with sensitive data deemed valuable in the cyber-criminal underworld.
A ransomware attack involves hacking into a network, encrypting its data, and demanding a ransom. It is typically paid with cryptocurrency to unlock it.
There have been countless attacks against hospitals, health plans, pharmaceutical laboratories, and other service providers in this area, in several countries:
- Utah Imaging Associates (UIA): a data breach affected 582,170 people, exposing their personal information.
- Highly confidential medical records leaked, including details of abortions, HIV tests, and mental health issues after a cyber-attack suffered by the NHS, the British National Health Service.
- A massive ransomware attack hit nine hospitals and healthcare institutions in Israel, disrupting service continuity.
- Hackers breached the Florida Department of Health (DOH-Broward) health system, exposing data on more than 1.3 million people who used their services.
- Grupo Fleury in Brazil, cyber-attack target, causing systems outage for several days, affecting customers and hospitals.
In addition to Information Security fragility in the health sector, numerous occurrences have origin in supply chains, showing how vulnerable hospitals and healthcare organizations are to hacker attacks. Regarding the cases above, two of them stemmed from supply chain attacks:
- Stor-A-File, a British data storage company whose clients include doctor practices, hospital funds, local councils, law firms, and accountants, was the source of the attack that resulted in an NHS data leak.
- In the case of DOH-Broward, attackers accessed computer networks through a third-party medical provider.
Regulations Might Help, But Are Not Enough
In the US, the breach notification rule under the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to disclose a breach if it affects more than 500 residents of a state or jurisdiction. According to HIPAA, an estimated 45 million health records were exposed or stolen in reported breaches in 2021 alone.
A Florida resident has filed a lawsuit against UF Health Central Florida after a data breach potentially exposed the information of more than 700,000 people. He accused the system of not adequately protecting the personally identifiable information of users of the health system.
IT leaders affirm that security is a top priority for organizations. However, the threat level has evolved and intensified, as have the methods used and the sophistication of attacks by cyber-criminals. Yet, from the Boards and other directors, there is still an understanding that safety means cost and not an investment that could prevent this type of occurrence, guaranteeing business continuity and protecting the interests of shareholders and other stakeholders.
Ransomware attacks has led the Boards of Directors and hospital executives to invest more in human resources, increasing the budget to face the cyber-security challenges. The mindset change in Information Security in Councils, which do not have the same experience in technology as in the technical area, is evolving rapidly. This shift is due to data leaks, threat scenarios, and operations stoppage, given the potential for damage from attacks on medical devices connected to their networks.
From March 2020 to September 2021, 82% of hospitals suffered cyberattacks targeting IoT devices. Even with low impacts, these attacks can be highly destructive. Recent trends in cyber-attacks emphasize the unavoidable and urgent need to strengthen cyber-security structures in healthcare organizations.
These threats suggest a unified security methodology for IT and OT. It must defend against evolving hazardous scenarios, addressing them, and eliminating vulnerable points.
Zero Trust: To Raise the Bar
Zero Trust architecture concept adoption is a path that tends to generate positive results. In the Zero Trust concept, no trust is assumed in networks, devices, or users, deploying a permanent real-time user authentication.
A survey by Symmetry Systems and Osterman Research released a report of 125 IT and security decision-makers in mid-sized and large organizations detailing how they plan to deploy Zero Trust architecture: 53% of respondents cited ransomware as its central motivator. Executives participating in the survey say that an architecture built on Zero Trust might increase cyber-security protections to prevent data breaches by up to 144%.
The digital transformation evidenced by the hyper-connectivity due to the increase in the number of mobile devices, cloud services, and remote work challenges the Zero Trust concept, increasing its adoption complexity.
The Brazilian Case
The first actions target some usual methods to carry out an attack. The adoption of passwordless authentication, guaranteeing the non-repudiation of the user, avoids a leading security vulnerability: credentials theft through phishing and malware attacks. This method will allow doctors, nurses, and other health professionals to access the hospital web portal without using passwords.
The hospital will implement a similar method so patients can access their exams in the future, further mitigating security risks and improving usability, as there will no longer be the need to use passwords.
Due to this challenging scenario, which will tend to worsen in the coming years, the largest hospital in the South of Brazil adopted Zero Trust.
IT professionals will access critical assets (servers, websites, databases, cloud services, and more) in a unique and safe interface. Users only access the systems necessary to carry out their activities, and they will not have access to systems credentials. This solution avoids accessing systems and devices out of the Critical Asset Management Platform. In a more robust security configuration for systems with a high degree of criticality, exclusive access through the Platform can be configured, thus preventing other types of attack such as DDoS (distributed denial-of-service).
Any access to systems, regardless of where they are (at the office or remotely), goes through a safe tunnel. It eliminates another potential risk from VPN (Virtual Private Network), vulnerable and used in several recent attacks. Also, it reduces the cost reduction by the overhead from VPN management.
The Platform also makes OT network management possible, especially new IoT equipment and devices that require an internet connection. The data processing in a critical IT system should be the same as hospital equipment since, increasingly, these two worlds begin to coexist to meet digital transformation demand through a single and integrated platform, easing management.
The Zero Trust architecture is not restricted only to hospital employees but also to the entire supply chain that, in some way, needs to access IT systems and hospital equipment. The chain constitutes one of the main problems, exposing how vulnerable their network is at that point.
In addition to robust security, Zero Trust architecture deployment additionally addresses General Data Protection Regulation compliance. It audits every action through logs, keylogging, and video session recording, enabling tracking in corporate systems.
Cybersecurity:
A Continuous Cycle
Promoting a cyber-security culture, as technical implementations, does not matter and cannot be left solely to the IT, but must be part of the institutional organization’s guideline as a whole and part of a continuous cycle.
The General Data Protection Law, in its lines, compelled for sensitive data correct handling and storage, turning it into an international trend. It undoubtedly increases healthcare data protection.
Hospitals save sensitive information in archives, medical records, laboratory and imaging tests, and various reports, demanding the adoption of cyber-security solutions robust enough to protect the rights of patients and other interested parties, mitigating the risks associated with the performance of your activities.
In the cases mentioned above, in which data breaches and leaks contained information of this kind, we can estimate the disruptive potential – in financial and reputational terms – that their misuse could cause to the healthcare institutions that control this data. It does not matter when in its systems or those on service providers.
Additionally, the General Data Protection Law determines sanctions on the controller that does not correctly maintain personal data under its provisions. The regulation lists punitive measures from a warning to penalties to the compulsory discontinuance of the organization’s business that violates its commandments.
Thus, healthcare organizations must adhere to solutions that prevent breaches and data leaks. Such technology should strengthen authentication to systems and devices, protecting patients’ data and its flow.
Healthcare must adopt technical and administrative measures following the best practices of Information Security, using data encryption at the source, to remain anonymous and strengthen Data Governance fostered by General Data Protection Act.
The technical measures aim to preserve operations, protect data and health services, and adapt them to the best practices and Information Security policies. It also ensures compliance with the Personal Data Protection regulations, such as the General Data Protection Act and recent IoT data regulations in the US and the UK. Unfortunately, there is no such similar regulation in Brazil, but soon it should take place as LGPD followed GDPR.
Return on Investment with Zero Trust
Reducing the Risk of Data Breach
Reducing the risk of data breach can reach up to 50%
Economy
In medium and large companies, savings can be as much as $20 per employee per month. Advanced Auditing can reduce by up to 25%.
Efficiency
Technical support calls can be reduced by up to 50%. Agility to deliver new infrastructure can be reduced by up to 80%.
GDPR – Overview of Fines and Penalties
2020

€ 1.240.000
Insufficient technical and organizational measures to ensure information security
2021

€ 107.000
Insufficient technical and organizational measures to ensure information security
2022

€ 152.000
Insufficient technical and organizational measures to ensure information security
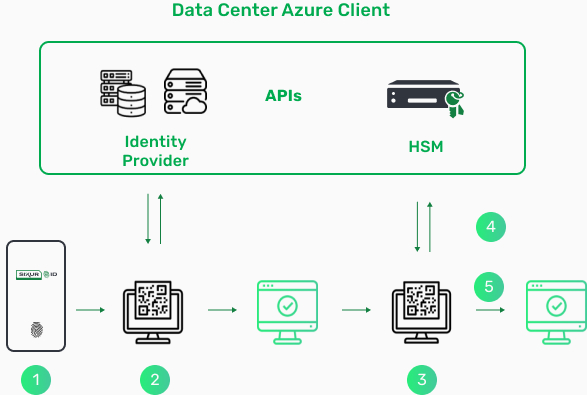
How it Works?

1 Stop using password in mobile app
2 End the use of login and password on the WEB
3 Transaction validation through cryptographic key
4 Data encryption at source
4 Transaction can be signed with the private key